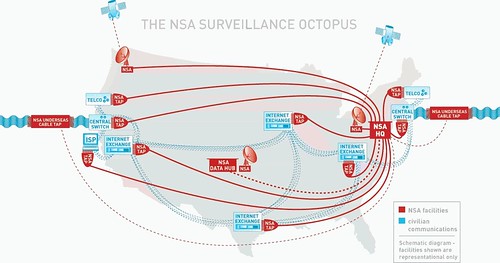
National Security Agency octupus conducts widespread surveillance of people in the United States and around the world. The US Senate recently gave broader authority to the state to carry out spying., a photo by Pan-African News Wire File Photos on Flickr.
June 11, 2013
A.C.L.U. Files Lawsuit Seeking to Stop the Collection of Domestic Phone Logs
By CHARLIE SAVAGE
New York Times
WASHINGTON — The American Civil Liberties Union sued the Obama administration on Tuesday over its “dragnet” collection of logs of domestic phone calls, contending that the once-secret program — whose existence was exposed last week by a former National Security Agency contractor — is illegal and asking a judge to stop it and order the records purged.
The lawsuit could set up an eventual Supreme Court test. It could also focus attention on this disclosure amid the larger heap of top secret surveillance matters revealed by Edward J. Snowden, the former N.S.A. contractor who came forward Sunday to say he was their source.
The program “gives the government a comprehensive record of our associations and public movements, revealing a wealth of detail about our familial, political, professional, religious and intimate associations,” the complaint says, adding that it “is likely to have a chilling effect on whistle-blowers and others who would otherwise contact” the A.C.L.U. for legal assistance.
The Justice Department declined to comment on the suit.
In other lawsuits against national security policies, the government has often persuaded courts to dismiss them without ruling on the merits by arguing that litigation would reveal state secrets or that the plaintiffs could not prove they were personally affected and so lacked standing in court.
This case may be different. The government has now declassified the existence of the program. And the A.C.L.U. is a customer of Verizon Business Network Services — the recipient of a leaked secret court order for all its domestic calling records — which it says gives it standing.
The call logging program keeps a record of “metadata” from domestic phone calls, including which numbers were dialed and received, from which location, and the time and duration.
The effort began as part of the Bush administration’s post-Sept. 11 programs of surveillance without court approval, which has continued since 2006 with the blessing of a national security court. The court has secretly ruled that bulk surveillance is authorized by a section of the Patriot Act that allows the F.B.I. to obtain “business records” relevant to a counterterrorism investigation.
Congress never openly voted to authorize the collection of logs of hundreds of millions of domestic calls, but some lawmakers were secretly briefed. Some members of Congress have backed the program as a useful counterterrorism tool; others have denounced it.
“The administration claims authority to sift through details of our private lives because the Patriot Act says that it can,” Representative F. James Sensenbrenner Jr., Republican of Wisconsin, wrote in a letter to Attorney General Eric H. Holder Jr. “I disagree. I authored the Patriot Act, and this is an abuse of that law.”
Over the weekend, James R. Clapper Jr., the director of national intelligence, said that officials may access the database only if they can meet a legal justification — “reasonable suspicion, based on specific facts, that the particular basis for the query is associated with a foreign terrorist organization.” Queries are audited under the oversight of the national security court.
Timothy Edgar, a former civil liberties official on intelligence matters in the Bush and Obama administrations who worked on building safeguards into the phone log program, said the notion underlying the limits was that people’s privacy is not invaded by having their records collected, but only when a human examines them.
“When you have important reasons why that collection needs to take place on a scale that is much larger than case-by-case or individual obtaining of records,” he said, “then one of the ways you try to deal with the privacy issue is you think carefully about having a set of safeguards that basically say, ‘O.K., yes, this has major privacy implications, but what can we do on the back end to address those?’ ”
Still, privacy advocates say the existence of the database will erode the sense of living in a free society: whenever Americans pick up a phone, they now face the consideration of whether they want the record of that call to go into the government’s files.
Moreover, while use of the database is now limited to terrorism, history has shown that new government powers granted for one purpose often end up applied to others. An expanded search warrant authority justified by the Sept. 11 attacks, for example, was used far more often in routine investigations like suspected drug, fraud and tax offenses.
Executive branch officials and lawmakers who support the program have hinted that some terrorist plots have been foiled by using the database. In private conversations, they have also explained that investigators start with a phone number linked to terrorism, and scrutinize the ring of people who have called that number — and other people who in turn called those — in an effort to identify co-conspirators.
Still, that analysis may generally be performed without a wholesale sweep of call records, since investigators can instead use subpoenas to obtain relevant logs from telephone companies. Senators Ron Wyden of Oregon and Mark Udall of Colorado, two Democrats who have examined it in classified Senate Intelligence Committee hearings, have claimed that the evidence is thin that the program provided uniquely available intelligence.
But supporters privately say the database’s existence is about more than convenience and speed. They say it can also help in searching for networks of terrorists who are taking steps to shield their communications from detection by using different phones to call one another. If calls from a different number are being made from the same location as calls by the number that was already known to be suspicious, having the entire database may be helpful in a way that subpoenas for specific numbers cannot match.
It remains unclear, however, whether there have been any real-world instances in which a terrorist was identified in that way, or whether that advantage is to date only theoretical.
A 1979 ruling over small-scale collection of calling metadata held that such records were not protected by the Fourth Amendment privacy rights since people have revealed such information to phone companies. In a 2012 case involving GPS trackers, however, the Supreme Court suggested that the long-term, automated collection of people’s public movements might raise Fourth Amendment issues.
No comments:
Post a Comment